Security Insights: Data Breaches — How to Respond in the First 24 Hours
Introduction
No organization — no matter how secure — is completely immune to data breaches.
From misconfigured cloud storage to sophisticated phishing attacks, breaches happen across every industry and scale.
What separates resilient companies from the rest is how they respond.
The first 24 hours after a breach are critical: the speed, accuracy, and transparency of your actions determine not only technical recovery but also legal, reputational, and financial outcomes.
This guide outlines what teams must do in that decisive first day to contain damage and restore trust.
Understanding the Impact
A data breach occurs when unauthorised parties access confidential or protected information — such as customer data, credentials, or intellectual property.
The consequences can include:
- Regulatory penalties (GDPR, HIPAA, etc.)
- Financial losses from business disruption
- Reputational damage and customer attrition
- Legal liability if due diligence wasn’t followed
The faster you detect, verify, and act, the lower the impact and potential exposure.
The Golden Window: The First 24 Hours
Incident response isn’t just a technical exercise — it’s a multi-disciplinary coordination effort involving IT, legal, communications, and leadership teams.
Here’s how to respond hour-by-hour in the critical first day.
0–2 Hours: Detection and Verification
1. Confirm the Breach
Not every alert is a breach.
- Validate the source of the alert (SIEM logs, IDS/IPS triggers, CloudTrail anomalies).
- Identify which systems or accounts are affected.
- Involve the Security Operations Center (SOC) or incident response (IR) team immediately.
2. Activate the Incident Response Plan
Trigger your IR protocol.
- Assign a breach coordinator or lead incident manager.
- Establish a secure internal communication channel (e.g., Signal, Slack war room).
- Disable compromised credentials or isolate affected servers to stop further intrusion.
2–6 Hours: Containment and Assessment
3. Contain the Breach
Goal: prevent further data exfiltration or system compromise.
- Block attacker IPs and revoke API keys.
- Segregate infected network segments.
- Take forensic snapshots before system changes.
- Change administrative credentials.
4. Identify the Scope and Data Exposure
Determine:
- What data was accessed or stolen.
- How long the attackers had access.
- Whether data was encrypted, hashed, or in plain text.
This phase establishes the technical footprint of the incident.
6–12 Hours: Notification and Coordination
5. Notify Internal Stakeholders
Inform leadership, legal counsel, and affected departments — not the public yet.
- Coordinate a single point of contact for updates.
- Begin drafting preliminary reports and talking points.
6. Engage External Partners
If needed, contact:
- Cybersecurity vendors for forensics and malware analysis.
- Law enforcement (CERT, FBI Cyber Division, local authorities).
- Cloud providers if breach occurred on hosted infrastructure.
Preserve all logs, evidence, and communications for compliance investigations.
12–18 Hours: Legal and Compliance Review
7. Consult Legal and Compliance Teams
Assess notification obligations under laws such as:
- GDPR: 72-hour notification requirement to regulators.
- CCPA: Breach disclosure for California residents.
- HIPAA: Patient data reporting for healthcare entities.
Work with counsel to define who needs to be notified and when.
Premature disclosure without verified details can worsen the situation.
18–24 Hours: Communication and Action
8. Prepare Public and Customer Statements
Coordinate a transparent and factual statement that includes:
- Nature of the breach
- Steps taken for containment
- Guidance for affected users (e.g., password resets, fraud alerts)
- Assurance of ongoing investigation
All public messaging should go through approved spokespersons — consistency prevents misinformation.
9. Begin Post-Incident Review
Even while containment continues, begin documenting:
- Root cause analysis (technical and procedural)
- Timeline of events
- Lessons learned for prevention
This documentation will support insurance claims, regulatory reporting, and future improvements.
Diagram: Data Breach Response - First 24 Hours Timeline
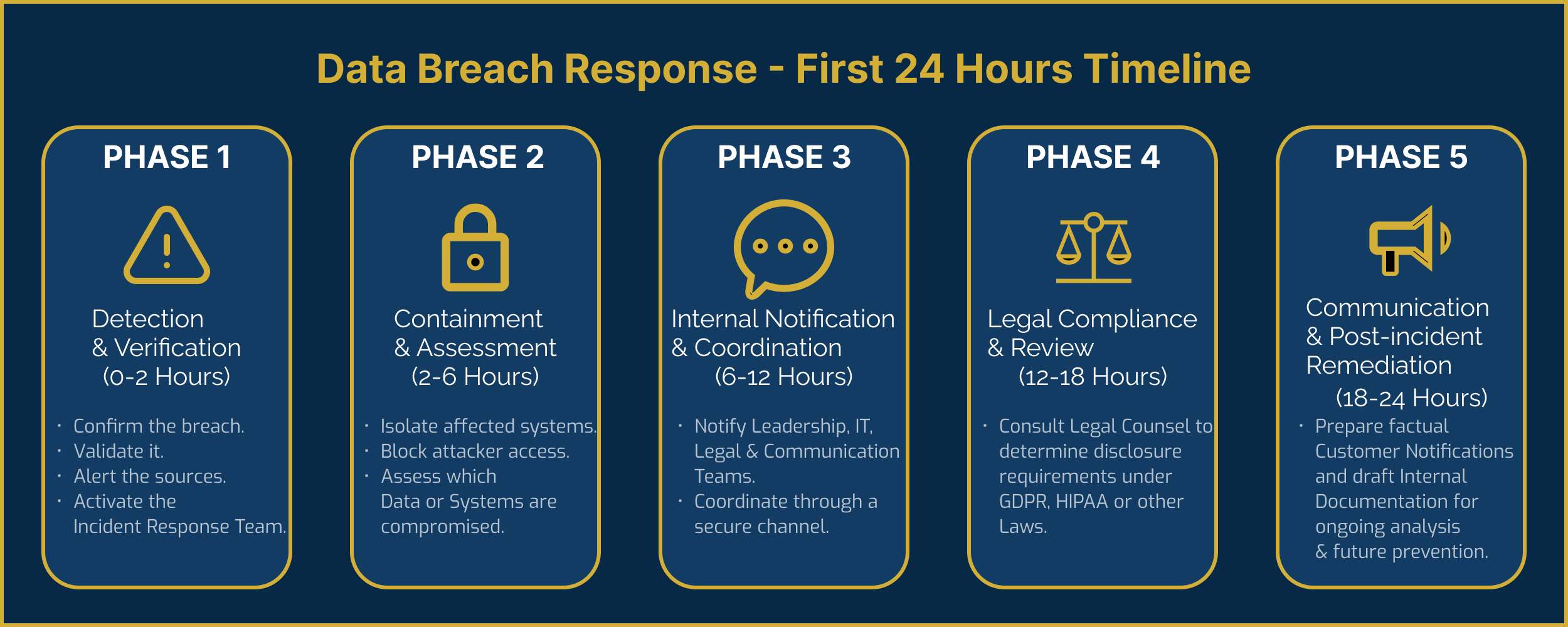
Figure: Data Breach Response - First 24 Hours Timeline
Common Mistakes to Avoid
- Deleting evidence before forensic investigation.
- Communicating inconsistently across departments or channels.
- Underestimating regulatory timelines (e.g., GDPR’s 72-hour rule).
- Neglecting internal coordination, leading to confusion or blame cycles.
- Over-promising to customers before facts are verified.
Strengthening Response Readiness
Being prepared means building a repeatable incident response framework long before a breach occurs.
Key elements include:
- A documented IR playbook with clear roles and escalation paths.
- Tabletop exercises simulating real-world attack scenarios.
- 24/7 monitoring via SIEM or managed detection tools.
- Regular employee training on phishing and data handling.
- Vendor risk management to assess third-party exposure.
The goal is not only to react fast — but to react right.
Conclusion
The first 24 hours after a data breach define whether your organization emerges resilient or shaken.
Swift containment, disciplined communication, and legal awareness make the difference between crisis and control.
Every incident should reinforce your defense — transforming a breach from a disaster into a lesson in digital resilience.





No comments yet. Be the first to comment!