AWS: Backup and Archival — Best Practices
Introduction:
Data loss is rarely caused by a single catastrophic event. In most real-world incidents, it happens due to misconfigurations, accidental deletions, ransomware, application bugs, or failed automation. As cloud adoption matures, backup and archival strategies are no longer optional safety nets — they are core architectural responsibilities.
AWS provides a rich set of native services for backup, snapshotting, replication, and long-term archival. However, many teams still approach backups as an afterthought, resulting in fragmented policies, inconsistent retention, and expensive storage sprawl.
This blog walks through practical AWS backup and archival best practices, focusing on how to design a reliable, cost-effective, and recoverable strategy — not just which services to enable.
Backup vs Archival — Understanding the Difference:
Before choosing services or writing policies, it’s critical to distinguish between backup and archival.
Backups are designed for:
- Short- to mid-term retention
- Fast recovery (minutes to hours)
- Operational resilience
Archival is designed for:
- Long-term retention (years)
- Compliance and audit requirements
- Extremely low cost with slower retrieval
Treating archival storage as a backup solution — or vice versa — leads to poor recovery outcomes and unnecessary cost.
Core AWS Backup Services You Should Know:
AWS offers multiple overlapping services. Knowing when to use which one is key.
AWS Backup
Centralized backup orchestration service that supports:
- EBS volumes
- RDS and Aurora
- DynamoDB
- EFS
- FSx
Key benefits:
- Policy-based backups
- Cross-account and cross-region support
- Backup vaults with access control
- Audit and compliance reporting
AWS Backup should be the default starting point for most workloads.
EBS Snapshots:
EBS snapshots are:
- Incremental
- Stored in S3 (managed by AWS)
- Used for fast EC2 volume restoration
Best practice:
- Automate via AWS Backup or lifecycle policies
- Never rely on manual snapshots for production
RDS & Aurora Automated Backups:
RDS provides:
- Point-in-time recovery
- Automated snapshots
- Transaction log backups
Important considerations:
- Automated backups are deleted when the DB is deleted
- Always create manual snapshots before destructive operations
Designing a Multi-Layer Backup Strategy:
A strong AWS backup design usually follows the 3-2-1 rule:
- 3 copies of data
- 2 different storage types
- 1 copy offsite (different region or account)
Recommended Layers
- Primary data (live workload)
- Local backup (same region)
- Secondary backup (cross-region or cross-account)
Cross-account backups are especially important to protect against accidental or malicious deletion.
Diagram: AWS Backup and Archival Architecture (Cross-Account & Cross-Region):
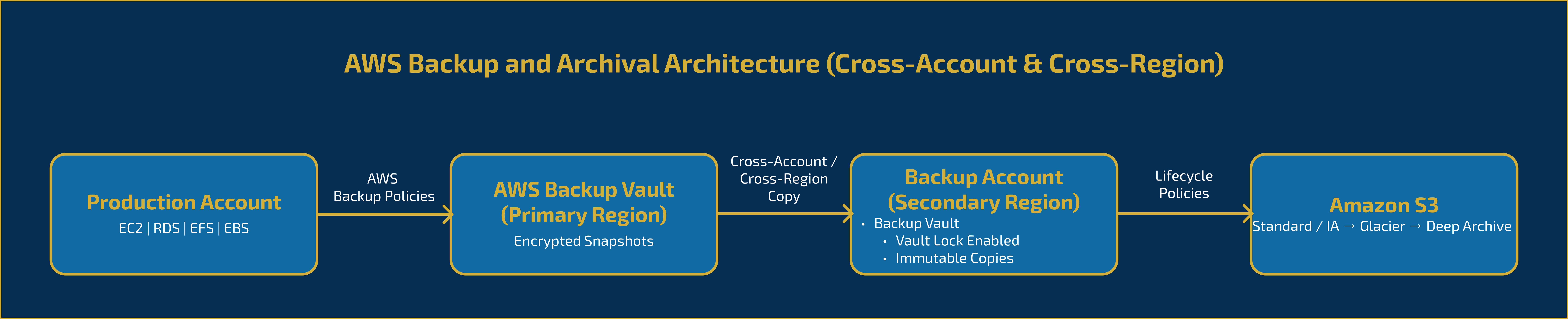
Figure: High-level AWS backup and archival architecture with cross-account, cross-region protection and long-term archival.
Using Cross-Account and Cross-Region Backups:
AWS Backup supports:
- Copying backups to another AWS account
- Copying backups to another region
Benefits:
- Protection against compromised accounts
- Disaster recovery readiness
- Compliance with geographic redundancy requirements
Example architecture:
- Production account → Backup account
- Primary region → Secondary region
Archival Strategy with Amazon S3:
Amazon S3 provides multiple storage classes suited for archival.
Key Archival Storage Classes
- S3 Glacier Instant Retrieval – low cost, fast access
- S3 Glacier Flexible Retrieval – minutes to hours retrieval
- S3 Glacier Deep Archive – lowest cost, 12–48 hour retrieval
Best practice:
- Use lifecycle policies to transition data automatically
- Never manually move objects for archival
Example — S3 Lifecycle Policy for Archival:
{
"Rules": [
{
"ID": "ArchiveAfter90Days",
"Status": "Enabled",
"Transitions": [
{
"Days": 90,
"StorageClass": "GLACIER"
},
{
"Days": 365,
"StorageClass": "DEEP_ARCHIVE"
}
]
}
]
}
This ensures data ages into cheaper tiers without operational overhead.
Security and Access Control Best Practices:
Backups are useless if they can be deleted or encrypted by attackers.
Critical Security Controls
- Enable AWS Backup Vault Lock (WORM protection)
- Use separate IAM roles for backup operations
- Restrict delete permissions aggressively
- Enable CloudTrail for backup-related actions
Vault Lock is especially important for ransomware resilience.
Testing Backups — The Most Ignored Step:
Many teams discover backup issues only during real incidents.
Best practices:
- Schedule periodic restore tests
- Automate test restores in non-production environments
- Validate application-level recovery, not just snapshot success
A backup that cannot be restored is not a backup.
Cost Optimisation for Backup and Archival:
Backup costs grow silently.
Optimisation techniques:
- Remove unused snapshots
- Tune retention periods
- Move older backups to Glacier
- Avoid over-retention “just in case”
AWS Backup reports and Cost Explorer should be reviewed monthly.
Common Mistakes to Avoid:
- Relying only on automated backups without manual checkpoints
- Keeping backups in the same account as production
- Ignoring restore testing
- Treating Glacier as a backup solution for operational recovery
- Forgetting application consistency (databases vs file snapshots)
Conclusion:
Backup and archival are not just operational concerns — they are architectural responsibilities. AWS provides powerful native tools, but their effectiveness depends on how thoughtfully they are combined.
A well-designed AWS backup strategy balances resilience, security, cost, and recoverability. Teams that invest early in structured backup and archival practices are far better prepared for outages, security incidents, and compliance audits.
In cloud architecture, the question is not if you’ll need your backups — it’s when.




No comments yet. Be the first to comment!